Setting up SSH on an IoT device router is a crucial step for securing and managing your network remotely. Whether you're a network administrator, a tech-savvy individual, or someone managing smart devices at home, understanding how to configure SSH for IoT devices is essential. Secure Shell (SSH) provides a secure communication channel, ensuring that your data remains encrypted and protected from unauthorized access. In this article, we will explore the step-by-step process of setting up SSH on IoT device routers, discuss its importance, and provide practical tips to enhance your network security.
IoT devices have become an integral part of modern life, from smart home appliances to industrial automation systems. These devices rely on routers to connect to the internet, making the router a critical component in ensuring seamless communication. However, without proper security measures, IoT devices can become vulnerable to cyberattacks. SSH is one of the most effective ways to secure your IoT device router, offering encrypted communication and remote access capabilities. In this guide, we will delve into the technical aspects of SSH setup while keeping the content accessible to readers of all expertise levels.
Before diving into the technical details, it's important to understand why SSH is vital for IoT device routers. Unlike traditional protocols such as Telnet, SSH encrypts all data transmitted between devices, making it nearly impossible for attackers to intercept sensitive information. This encryption is particularly important for IoT devices, which often handle sensitive data like user credentials, health metrics, or industrial control commands. By the end of this article, you will have a clear understanding of how to set up SSH on your IoT device router and why it is a critical step in safeguarding your network.
Table of Contents
- Introduction to SSH
- Why SSH is Important for IoT Devices
- Prerequisites for Setting Up SSH
- Step-by-Step SSH Setup
- Best Practices for SSH Configuration
- Troubleshooting Common SSH Issues
- Enhancing Security with SSH Keys
- Monitoring and Maintaining SSH
- Future Trends in SSH and IoT Security
- Conclusion
Introduction to SSH
Secure Shell (SSH) is a cryptographic network protocol used for secure data communication, remote command execution, and other secure network services. It was designed as a replacement for less secure protocols like Telnet and FTP, which transmit data in plain text. SSH operates on the client-server model, where the client initiates a connection to the server. Once the connection is established, all data exchanged between the client and server is encrypted, ensuring confidentiality and integrity.
SSH is widely used in various applications, including remote server management, file transfers, and tunneling. Its versatility makes it an ideal choice for securing IoT device routers. By enabling SSH, you can remotely manage your router's settings, monitor network activity, and troubleshoot issues without exposing your network to potential threats. SSH also supports authentication methods like passwords and public-key cryptography, providing an additional layer of security.
One of the key advantages of SSH is its ability to create secure tunnels. These tunnels can be used to forward traffic from one network to another, allowing you to access internal network resources securely. For IoT devices, this feature is particularly useful as it enables secure communication between devices located in different geographical locations. In the next section, we will discuss why SSH is indispensable for IoT devices and how it enhances their security.
Why SSH is Important for IoT Devices
IoT devices are often deployed in environments where they are exposed to various security risks. These devices are connected to the internet, making them potential targets for cybercriminals. Without proper security measures, attackers can exploit vulnerabilities in IoT devices to gain unauthorized access, steal sensitive data, or disrupt network operations. SSH plays a vital role in mitigating these risks by providing a secure communication channel.
One of the primary reasons SSH is important for IoT devices is its ability to encrypt data. Encryption ensures that even if an attacker intercepts the data transmitted between the IoT device and the router, they cannot decipher it without the encryption key. This is particularly important for devices that handle sensitive information, such as medical devices, smart locks, or industrial sensors. By enabling SSH, you can ensure that all communication between your IoT devices and the router remains confidential.
Another advantage of SSH is its support for strong authentication mechanisms. Unlike traditional protocols that rely solely on passwords, SSH allows you to use public-key cryptography for authentication. This method involves generating a pair of cryptographic keys: a private key stored on the client and a public key stored on the server. The use of cryptographic keys makes it significantly harder for attackers to gain unauthorized access, as they would need to compromise both the private and public keys.
Prerequisites for Setting Up SSH
Before you begin setting up SSH on your IoT device router, there are several prerequisites you need to fulfill. These include ensuring that your router supports SSH, having administrative access to the router, and preparing the necessary tools and software. Let's explore these prerequisites in detail.
First and foremost, you need to confirm that your router supports SSH. Most modern routers come with built-in SSH capabilities, but older models may not have this feature. To check if your router supports SSH, refer to the manufacturer's documentation or access the router's web interface. If your router does not support SSH, you may need to upgrade its firmware or consider purchasing a new router that supports this protocol.
Next, ensure that you have administrative access to the router. This typically involves logging in to the router's web interface using the admin credentials. If you are unsure of the login details, consult the router's manual or contact the manufacturer's support team. Administrative access is essential for configuring SSH settings and making changes to the router's security policies.
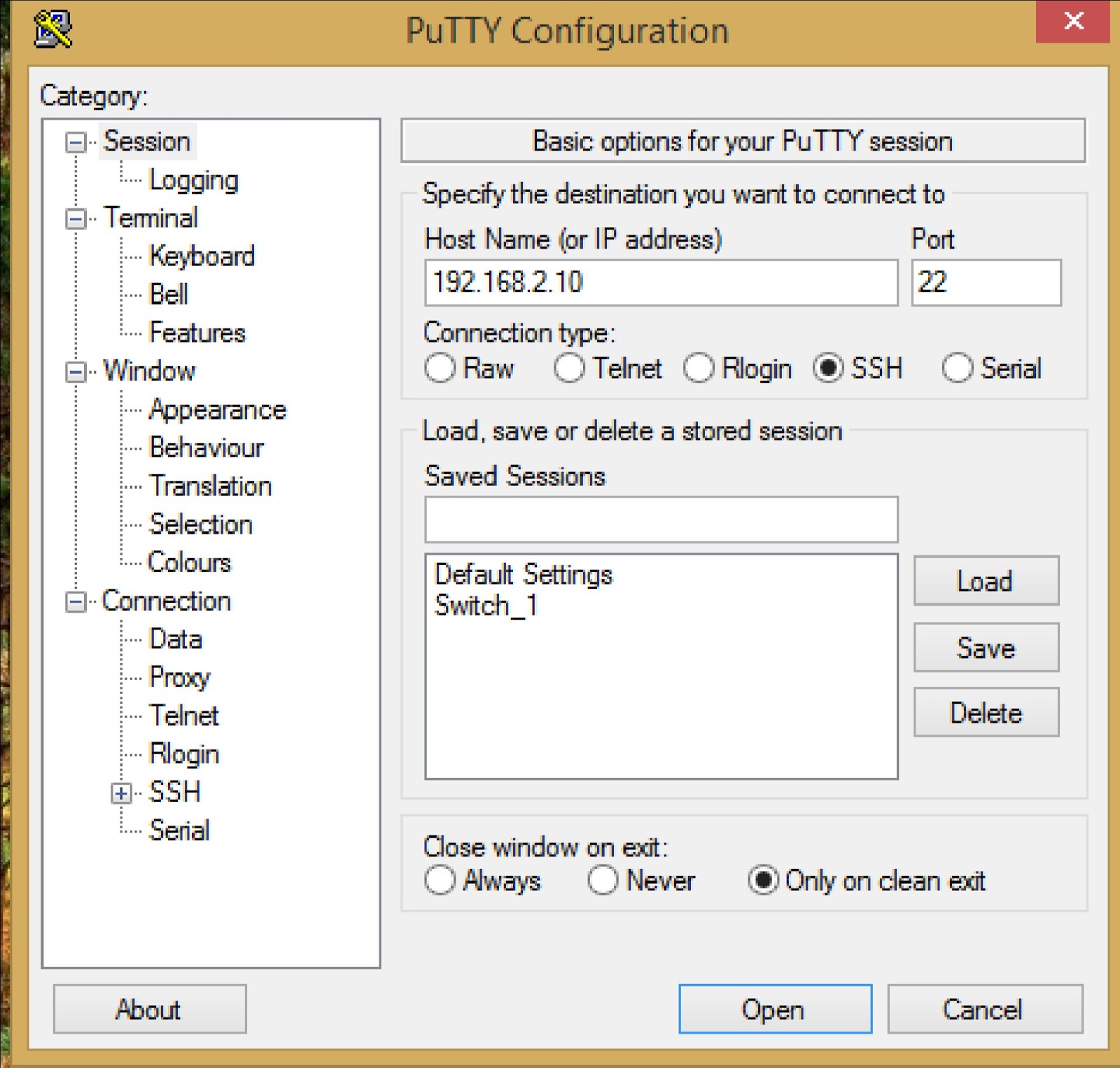
Finally, prepare the necessary tools and software for setting up SSH. This includes a computer or device with an SSH client installed, such as PuTTY for Windows or the built-in Terminal for macOS and Linux. You may also need a text editor to create and manage SSH keys if you plan to use public-key authentication. Once you have fulfilled these prerequisites, you are ready to proceed with the SSH setup.
Step-by-Step SSH Setup
Setting up SSH on your IoT device router involves several steps, from accessing the router to configuring SSH settings. In this section, we will guide you through the process in detail.
Accessing the Router
The first step in setting up SSH is accessing the router's web interface. To do this, open a web browser and enter the router's IP address in the address bar. The default IP address is usually printed on the router's label or mentioned in the user manual. If you are unsure, try common addresses like 192.168.0.1 or 192.168.1.1.
Once you have accessed the web interface, log in using the admin credentials. If you have not changed the default username and password, refer to the router's documentation to find these details. After logging in, navigate to the settings section where you can enable SSH. The location of this setting may vary depending on the router's brand and model.
Configuring SSH Settings
After enabling SSH, you need to configure its settings to ensure optimal security. Start by changing the default SSH port from 22 to a non-standard port. This simple step can help reduce the risk of automated attacks targeting port 22. Next, disable password authentication and enable public-key authentication. This ensures that only devices with the correct private key can access the router via SSH.
Generate an SSH key pair using your computer's terminal or an SSH client. The private key should be stored securely on your device, while the public key should be uploaded to the router. To upload the public key, navigate to the SSH settings section in the router's web interface and paste the key into the designated field. Save the changes and restart the router to apply the new settings.
Finally, test the SSH connection by using your SSH client to connect to the router. If the connection is successful, you have successfully set up SSH on your IoT device router. If you encounter any issues, refer to the troubleshooting section later in this article.
Best Practices for SSH Configuration
To maximize the security of your SSH setup, it's important to follow best practices. These include using strong passwords, limiting access to trusted IP addresses, and regularly updating the router's firmware. Let's explore these practices in detail.
First, always use strong passwords for your router's admin account and SSH key passphrase. A strong password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information like your name or birthdate. If you are using public-key authentication, ensure that your private key is protected with a strong passphrase.
Next, limit SSH access to trusted IP addresses. This can be done by configuring the router's firewall to allow SSH connections only from specific IP addresses. This reduces the risk of unauthorized access from unknown sources. Additionally, consider disabling root login and creating a separate user account with limited privileges for SSH access.
Finally, keep your router's firmware up to date. Manufacturers frequently release firmware updates to patch security vulnerabilities and improve performance. Regularly check for updates and apply them as soon as they become available. This ensures that your router remains secure against the latest threats.
Troubleshooting Common SSH Issues
While setting up SSH, you may encounter several common issues. These include connection failures, authentication errors, and performance problems. In this section, we will discuss how to troubleshoot these issues effectively.
One of the most common issues is a failed SSH connection. This can occur due to incorrect settings, firewall restrictions, or network issues. To resolve this, double-check the router's SSH settings, including the port number and authentication method. Ensure that the firewall is configured to allow SSH traffic and that your network connection is stable.
Authentication errors are another frequent problem. These can occur if the private key does not match the public key or if the passphrase is incorrect. To fix this, verify that the correct private key is being used and that the passphrase is entered accurately. If you are using password authentication, ensure that the password is correct and meets the router's complexity requirements.
Performance issues, such as slow connection speeds, can also occur. This may be due to network congestion, high latency, or insufficient router resources. To address this, try connecting to the router during off-peak hours, use a wired connection instead of Wi-Fi, and ensure that the router's hardware is capable of handling SSH traffic efficiently.
Enhancing Security with SSH Keys
Using SSH keys for authentication is one of the most effective ways to enhance the security of your IoT device router. Unlike passwords, SSH keys are nearly impossible to guess or brute-force, making them a more secure option. In this section, we will discuss how to generate and manage SSH keys.
To generate an SSH key pair, open your computer's terminal and run the command ssh-keygen. This will prompt you to choose a location to save the keys and enter a passphrase. Once the keys are generated, copy the public key to the router's web interface and paste it into the SSH settings section. The private key should be stored securely on your device and never shared with others.
Managing SSH keys involves regularly rotating them to minimize the risk of compromise. This can be done by generating a new key pair and replacing the old keys on the router. Additionally, ensure that the private key is backed up in a secure location, such as an encrypted USB drive or cloud storage service. By following these practices, you can maintain a high level of security for your SSH setup.
Monitoring and Maintaining SSH
Once SSH is set up on your IoT device router, it's important to monitor and maintain it regularly. This includes reviewing logs, updating configurations, and performing security audits. Let's explore these tasks in detail.
Reviewing logs is an essential part of monitoring SSH activity. Most routers provide logs that record SSH connection attempts, successful logins, and other relevant events. Regularly check these logs to identify any suspicious activity, such as repeated failed login attempts or connections from unknown IP addresses. If you notice any anomalies, take immediate action to investigate and resolve the issue.
Article Recommendations